Thursday, September 30, 2010
Health Wonk Review at Healthcare Talent Transformation
Peggy Salvatore posts the latest Health Wonk Review - the best of the healthcare policy blogosphere.
Labels:
Health Wonk Review
Tuesday, September 28, 2010
ONC releases FAQ on EHR Certification
Question [9-10-001-1]: What certification criteria will ONC-ATCBs use to certify EHR technology for purposes of the “deeming” provision of the Physician Self-Referral Prohibition and Anti-Kickback Electronic Health Record (EHR) Exception and Safe Harbor Final Rules?
Question [9-10-002-1]: If my EHR technology is capable of submitting batch files to an immunization registry using the adopted standards (HL7 2.3.1 or 2.5.1 and CVX), is that sufficient for demonstrating compliance with the certification criterion specified at 45 CFR 170.302(k)?
Question [9-10-003-1]: In the “Initial Set of Standards, Implementation Specifications, and Certification Criteria for Electronic Health Record Technology” Final Rule published on July 28, 2010, the Secretary adopted the following implementation specifications at 45 CFR 170.205(d)(2) for HL7 2.5.1 – Public Health Information Network HL7 Version 2.5 Message Structure Specification for National Condition Reporting Final Version 1.0 and Errata and Clarifications National Notification Message Structural Specification. We believe that these implementation specifications may have been adopted in error because they only provide direction to public health agencies on how to report to the Centers for Disease Control and Prevention (CDC). Therefore, their adoption does not appear to either provide the appropriate or requisite implementation guidance for the adopted standard, HL7 2.5.1, or more importantly, to enable the user to “electronically record, modify, retrieve, and submit syndrome-based public health surveillance information…,” as required by the adopted certification criterion, 45 CFR 170.302(l). Please clarify whether these implementation specifications are appropriate for the intended capability specified by the public health surveillance certification criterion at 45 CFR 170.302(l)?
Question [9-10-004-1]: I currently use EHR version 1.3 which I purchased from EHR technology developer XYZ. EHR technology developer XYZ has informed me that it is not going to seek certification for EHR version 1.3. Can I seek certification for EHR version 1.3 or can I partner with a group of other health care providers that also use version 1.3 to split the cost of certification? Additionally, if EHR version 1.3 becomes certified can anyone else using EHR version 1.3 rely on the certification issued to EHR version 1.3?
Question [9-10-005-1]: I am an EHR technology developer. I have sought and achieved certification for the Complete EHR that I sell. The Complete EHR, however, is also designed to be sold in separate components so that I can offer my customers different prices based on the capabilities they seek to implement. Is it possible for me to sell components of my certified Complete EHR separately as certified EHR Modules, or do I need to seek testing and certification for each of the separate components that I plan to sell as certified EHR Modules?
Question [9-10-006-1]: I submitted a Complete EHR for certification, but it has not passed a test for one or more of the certification criteria. Can I request that the ONC-ATCB certify the EHR technology that I submitted as an EHR Module instead (i.e., certify only those capabilities that have been tested successfully)?
Question [9-10-007-1]: My hospital purchased a certified EHR Module that provides approximately 75% of the capabilities we need to meet the definition of Certified EHR Technology. The other 25% are provided by our own self-developed system(s). Can we have our self-developed system tested and certified as an EHR Module and then subsequently use the combination of our self-developed certified EHR Module with the certified EHR Module we purchased to meet the definition of Certified EHR Technology? As a follow up, do we need to have the combination of the purchased certified EHR Module and our self-developed certified EHR Module tested and certified together as a Complete EHR (above and beyond the certifications they have already been issued)?
Question [9-10-008-1]: If an EHR Module addresses multiple certification criteria (thus providing multiple capabilities), does it need to be tested and certified to the applicable privacy and security certification criteria as a whole or for each capability?
Question [9-10-009-1]: I'm an EHR technology developer and I've had my Complete EHR certified. I work with business partners/distributors and permit them to sell my (unmodified) certified Complete EHR under their own brand/name/label. Is this business practice permitted? Is there anything that I should do or be aware of?
Question [9-10-010-1]: My EHR technology is designed to receive demographic data from a registration system or a practice management system. The data from these other IT systems is then used by my EHR technology to demonstrate compliance with one or more certification criteria. Do these other IT systems that act as data sources to my EHR technology need to be certified?
Question [9-10-011-1]: I’ve identified that I am using two different EHR technologies to meet a single certification criterion (my document management system receives and displays summary records (45 CFR 306(f)(1)) and my EHR technology from EHR technology developer XYZ transmits summary records (45 CFR 306(f)(2)). Do both EHR technologies need to be certified?
Question [9-10-012-1]: How many clinical quality measures must EHR technology be capable of calculating in order to get certified?
Question [9-10-013-1]: I plan on sending/transferring meaningful use quality reporting data from my EHR technology to my “data warehouse” and have the data warehouse submit/report out the data to CMS. Does my data warehouse need to be certified?
Question [9-10-014-1]: I’ve selected a certified Complete EHR [or certified EHR Module] from EHR technology developer XYZ. That being said, I prefer the certified CPOE EHR Module designed by EHR technology developer ABC over the CPOE capability included in EHR technology developer XYZ’s Complete EHR. Can I use the certified CPOE EHR Module from EHR technology developer ABC instead of the CPOE capability included in EHR technology developer XYZ’s certified Complete EHR? Alternatively, can I use both of the certified CPOE capabilities included in EHR technology developer XYZ and ABC’s EHR technologies at the same time? In other words, can I use duplicative or overlapping certified capabilities of different certified EHR technologies without jeopardizing my ability to meaningfully use Certified EHR Technology?
Question [9-10-015-1]: I am an EHR technology developer preparing my EHR technology for certification. I am relying on a 3rd party software program to demonstrate my compliance with a specific certification criterion. Does this 3rd party software program need to be independently certified?
Question [9-10-016-1]: I’m in the process of implementing EHR technology developer XYZ’s certified Complete EHR [or certified EHR Module] “E-HealthSystem2010.” Scenario 1: I have determined that E-HealthSystem2010 needs to be reconfigured in order to connect with one of my patient registration systems. Can I reconfigure E-HealthSystem2010 without compromising the certified status of my implementation of E-HeatlhSystem2010? Scenario 2: EHR technology developer XYZ communicated to my organization that they relied upon a 3rd party software program “PatientInfoTracker 2.0” for the purposes of demonstrating compliance with the “generate patient lists” certification criterion specified at 45 CFR 170.302(i) in achieving E-HeatlhSystem2010’s certification. I have already implemented, use, and would like to continue using “SuperListGenerator 7.0.” I have determined that I can reconfigure SuperListGenerator 7.0 to work with E-HeatlhSystem2010. Can I use SuperListGenerator 7.0 in lieu of PatientInfoTracker 2.0 without compromising the certified status of my implementation of E-HeatlhSystem2010?
Question [9-10-017-1]: Under the Medicare and Medicaid EHR Incentive Programs Final Rule, eligible health care providers are permitted to defer certain meaningful use objectives and measures and still receive an EHR incentive payment. However, it is our understanding that in order for us to have our EHR technology certified, we must implement all of the applicable capabilities specified in the adopted certification criteria regardless of whether we intend to use all of those capabilities to qualify for our EHR incentive payment. Is our understanding correct?
Question [9-10-018-1]: I use or would like to use an “interface” to submit data to a public health agency/registry. Does this interface need to be certified?
Question [9-10-019-1]: The “electronic copy of health information” certification criteria (45 CFR 170.304(f) and 45 CFR 170.306(d)) each require that Certified EHR Technology “enable a user to create an electronic copy of a patient’s clinical information… in: (1) Human readable format; and (2) On electronic media or through some other electronic means….” Is there more than one way to demonstrate compliance with these certification criteria?
Question [9-10-020-1]: The certification criterion at 45 CFR 170.302(n) specifies that “[f]or each meaningful use objective with a percentage-based measure, electronically record the numerator and denominator and generate a report including the numerator, denominator, and resulting percentage associated with each applicable meaningful use measure.” Is it possible for the action of “record” in the certification criterion to be implemented in different ways and still remain in compliance with the certification criterion? For example, could “record” comprise the ability of a centralized analytics EHR Module to accept or retrieve raw data from another EHR Module or EHR Modules, and upon receipt of this raw data, the centralized analytics EHR Module would calculate the numerator, denominator, and the resulting percentage as specified by 45 CFR 170.302(n)?
Additional FAQs
Labels:
ONC
Tuesday, September 21, 2010
The September HIT Standards Committee
by John Halamka, Life as a Healthcare CIO
The September HIT Standards Committee included three major topics, all of which are important for "living the dream" of achieving meaningful use in the real world.
First, Jamie Ferguson and Betsy Humphreys briefed the committee on the recent Vocabulary Task Force Hearings which focused on reducing barriers and creating enablers to accelerate interoperability. One such enabler is creating a "one Stop shopping" resource for downloading the vocabularies and codesets required by the Standards Final Rule. Major themes included from the hearings included:
*Clarity about what is required, of whom, for what intended purpose and future vision is more important than simplicity
*A comprehensive plan does not mean it should be done all it once. Phased implementation of prioritized content sets and maps will ease adoption burdens
*A major issue reported by testifiers were intellectual property barriers to making these tools widely available. For examples, there are mappings that are only available to licensed users of proprietary vocabularies (i.e. RxNorm to First Data Bank mapping) and some code sets are embedded in HL7 and NCPDP standards which are only available via yearly membership in those organizations.
Vocabularies are increasingly important and Betsy Humphreys reported that licensure of UMLS for access to SNOMED-CT and RxNorm has grown tremendously - the final rule has accelerated adoption of controlled terminology. Thus, it is important that resources that facilitate the implementation and maintenance of meaningful use vocabularies are important.
Several ideas for addressing intellectual property issues were discussed including government licensure of vocabularies for general use and centralized procurement/license management for vocabularies needed for meaningful use that reduces the burden on hospitals and eligible professionals.
Judy Murphy and Liz Johnson presented the Implementation Workgroup's key priorities for the next year which include information sharing and communication to reduce the burden of achieving meaningful use. Hospitals and eligible professionals have similar questions, frustrations, and change management challenges. By leveraging the wisdom of the crowd via novel social networking approaches and education, we can accelerate the process for all.
Doug Fridsma presented the Standards and Interoperability Framework, the RFPs that have been awarded, and processes that will be defined to ensure that clear, easy to use implementation guides are available in the future.
Next month we'll hear from the HIT Policy Committee so that we can begin the standards selection effort in support of Meaningful Use Stage 2 and 3. The industry needs a phased implementation plan and thus my preference would be to declare what is needed for stage 3 and then define stage 2 as the incremental steps to get us on the right trajectory.
Labels:
HIT Standards Committee,
John Halamka
50.7 million uninsured in 2009
The number of Americans without health insurance coverage increased to 50.7 million in 2009, from 46.3 million in 2008. The percentage of uninsured increased as well to 16.7 percent, from 15.4 percent over the same period.
Other highlights include:
- "The number of people with health insurance decreased from 255.1 million in 2008 to 253.6 million in 2009. Since 1987, the first year that comparable health insurance data were collected, this is the first year that the number of people with health insurance has decreased.
- Between 2008 and 2009, the number of people covered by private health insurance decreased from 201.0 million to 194.5 million, while the number covered by government health insurance climbed from 87.4 million to 93.2 million. The number covered by employment-based health insurance declined from 176.3 million to 169.7 million. The number with Medicaid coverage increased from 42.6 million to 47.8 million.
- Comparable health insurance data were first collected in 1987. The percentage of people covered by private insurance (63.9 percent) is the lowest since that year, as is the percentage of people covered by employment-based insurance (55.8 percent). In contrast, the percentage of people covered by government health insurance programs (30.6 percent) is the highest since 1987, as is the percentage covered by Medicaid (15.7 percent).
- In 2009, 10.0 percent (7.5 million) of children under 18 were without health insurance. Neither estimate is significantly different from the corresponding 2008 estimate.
- The uninsured rate for children in poverty (15.1 percent) was greater than the rate for all children.
- In 2009, the uninsured rates decreased as household income increased: from 26.6 percent for those in households with annual incomes less than $25,000 to 9.1 percent in households with incomes of $75,000 or more.
- The proportion of the foreign-born population without health insurance in 2009 was nearly two-and-a-half times that of the native-born population."
Labels:
Health Insurance Coverage
Thursday, September 16, 2010
Politics, Money and Health
Check out the latest Health Wonk Review - the best of the healthcare policy blogosphere - hosted by Louise Norris at Colorado Health Insurance Insider. There are some terrific posts on healthcare costs, the politics of healthcare and the economics of healthcare.
Labels:
Health Wonk Review
Rave Review - ADP & Capital C
 In a break from HTN's usual fare...
In a break from HTN's usual fare... Check out the latest Indie up & comer - ADP and Capital C's "The Dope Sauce" EP, with a rave review from Brianna Smith, The New York Examiner's Indie Music critic:
"They've tagged their music as "chillwave, raw hip hop beats, and Brooklyn." That doesn't even begin to describe how sick these songs are. There's an infusion of jazz/funk hooks, glitch-hop, and flawless drum beats. It's a Sunday afternoon in Brooklyn at a block party, but not the wild-too-drunk-kind, the kind where your whole family is there, and you're smoking and laying out on thrifted patio furniture and you're thinking to yourself that nothing could be better than that moment. ADP is in your neighborhood. It's impossible to pick a favorite track off of this EP, as they are all so unique. There is no doubt that if they continue to produce tracks like this, they will get used by every great remix and hip-hop artist out there. The thought of RZA or Mos Def or ODB sampling these tracks is blwoing me out of my skull."
The download is available here.
Labels:
ADP,
Capital C,
The Dope Sauce
Tuesday, September 14, 2010
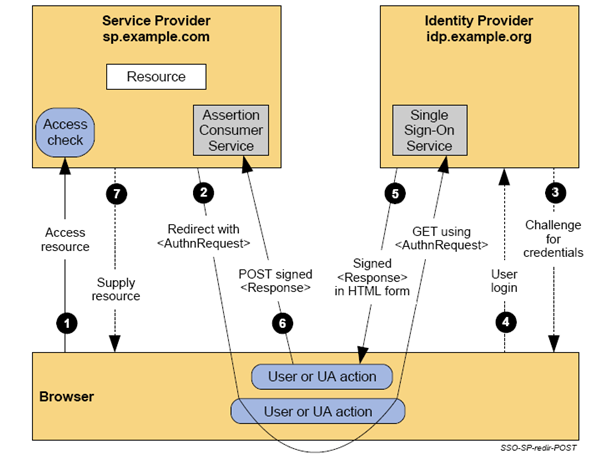
SAML's Rise
The Secure Assertion Markup Language (SAML) is a federated XML framework for the exchange of security and identity information across domains. "As its name suggests, SAML allows business entities to make assertions regarding the identity, attributes, and entitlements of a subject (an entity that is often a human user) to other entities, such as a partner company or another enterprise application."
The IETF Journal has a good orientation article on SAML ("It's the F Word") , excerpted below.
 "As relationships among enterprises, service providers, and users became more interdependent, the challenge of obtaining lookup permissions from outside of an organization grew. In this new world, in order for a service in organization A to be able to accept users from organization B, the service in organization A needs permission to look up users in organization B’s directory. Even if the number of organization A’s and services is small, the problem of controlling access to organization B’s directories quickly becomes unmanageable.
"As relationships among enterprises, service providers, and users became more interdependent, the challenge of obtaining lookup permissions from outside of an organization grew. In this new world, in order for a service in organization A to be able to accept users from organization B, the service in organization A needs permission to look up users in organization B’s directory. Even if the number of organization A’s and services is small, the problem of controlling access to organization B’s directories quickly becomes unmanageable.Initially the solutions seemed to focus on Web applications (for the most part, they still do, though that is starting to change). Toward the end of the 1990s, the need to manage centralized authentication for Web applications drove the development of the so-called enterprise Web single sign-on solutions.
Out of those solutions a number of open-source and commercial options evolved, many of which relied on the management of HTTP cookies. Those solutions were also intraorganizational in nature and, as the need to connect Web SSO (single sign-on) products across organizational boundaries grew, there arose a need for a standardized protocol for communication authentication information between applications.
In January 2001, the OASIS Security Services Technical Committee (SSTC) convened to begin work on what became SAML (security assertion markup language), a technology that has become one of the cornerstones of federated authentication.
SAML can support several use-cases but the most commonly deployed pattern is called Browser Web SSO. This particular profile of SAML involves three actors: the user, the identity provider, and the service provider. SAML uses XML-based messages and relies on public key cryptography (although not necessarily on public key infrastructure [X.509] or PKIX) to sign and encrypt those messages. In a typical authentication flow the user presents credentials to the identity provider (IdP), thereby proving her identity to the IdP. The IdP then gives the user a SAML message called an assertion, digitally signed with the key of the IdP and optionally encrypted with the key of the service provider. The assertion can be thought of as a sealed envelope containing a statement to the effect that the user has successfully authenticated herself as well as the properties of the user the IdP wants to make known to the service provider. If the service provider trusts the public key of the IdP, the service provider is able to consume the assertion. The assertion often contains an identifier of the user and-more important-additional attributes associated with the user, relieving the service provider from having to conduct additional lookups in directories.
In the SAML federation model, identity information-identifiers and additional attributes-is pushed from the IdP to the SP. Conversely, enterprise authentication operates according to a pull model. This might seem a small difference but it fundamentally changes the way applications (service providers) consume identities.
At this point, the astute reader will undoubtedly ask: “But what about key management?” Indeed, key management is the core of the matter. Some federations still rely on traditional PKIX-style hierarchical PKI for key management. Others, including many large-scale SAML federations, rely on an alternative key-management method. In this method, collections of keys are collectively signed, resulting in an object that behaves like a combination of a PKI certificate and CRL (certificate revocation list). Incidentally, this bag-of-keys model has been considered by the KARP (Keying and Authentication for Routing Protocols) working group as the basis for routing protocol key management (albeit in that case using symmetric keys).
Common to all approaches to key management is a federation that consists of those identity providers and service providers that share trust in a set of keys. Such a trust framework is called a ring of trust. The deployment of OpenID typically relies on a single global ring of trust that encompasses all OpenID IdPs, and SPs. In fact, it is entirely possible that the success of OpenID is due in large part to the absence of a requirement on key management. Conversely, SAML federations often do require key-and-trust management, which constitutes a major part of the work involved in running a SAML federation."
Eve Maler prepared the following overview charts on SAML components:

Labels:
SAML
Tuesday, September 7, 2010
Total 2010 Health benefit costs up 3% but employee costs up 14%
Some striking trends in Employer Health Benefits were highlighted in the Kaiser Family Founding and Health Research Education Trust survey including:
Workers on average are paying nearly $4,000 this year toward the cost of family health coverage - an increase of 14 percent, or $482, above what they paid last year.
The jump occurred even though the total premiums for family coverage, including what employers themselves contribute, rose a modest 3 percent to $13,770 on average in 2010. In contrast, the amount employers contribute for family coverage did not increase.
Preferred Provider Organizations (PPOs) continue to dominate the employer market, enrolling 58 percent of covered workers. Average PPO family premiums topped $14,000 annually in 2010.
Since 2005, workers’ contributions to premiums have gone up 47 percent, while overall premiums rose 27 percent, wages increased 18 percent, and inflation rose 12 percent.
Many employers are also raising the annual deductibles workers must pay before their health plans begin to share most health care costs. A total of 27 percent of covered workers now face annual deductibles of at least $1,000, up from 22 percent in 2009. Among small firms (3-199 workers), 46 percent face such deductibles.
30 percent of employers say they reduced the scope of health benefits or increased cost sharing, and 23 percent report increasing the amount employees pay for coverage.
Among other plan types, only consumer-driven plans (which are high-deductible plans that also include a tax-preferred savings options such as a Health Savings Account or Health Reimbursement Arrangement) saw growth in their market share. Such plans now enroll 13 percent of covered workers, up from 8 percent last year.
Other findings include:
• Single coverage. The survey also tracks the premiums for worker-only health benefits, which increased 5 percent in 2010 to reach $5,049 annually. Workers on average are paying $899 annually for single coverage, up from $779 in 2009. Forty-seven percent of covered workers are in single coverage plans.
• Physician office visits. Among covered workers with a copayment for in-network physician office visits, the average copayment increased a small but statistically significant amount from 2009 to 2010 -- from $20 to $22 for primary care and from $28 to $31 for specialty care.
• Mental health benefits. In response to the 2008 Mental Health Parity and Addiction Equity Act, 31 percent of firms with more than 50 workers made changes to the mental health benefits they offer. Most of this group eliminated limits on coverage to comply with the law, though a small share (5 percent of those making changes) dropped mental health coverage altogether.
• Wellness benefits. About three-fourths (74 percent) of employers offering health benefits offer at least one of the following wellness programs: weight loss program, gym membership discounts or on-site exercise facilities, smoking cessation program, personal health coaching, classes in nutrition or healthy living, web-based resources for healthy living, or a wellness newsletter.
• Health risk assessments. Among firms offering coverage, 11 percent give their employees the option of completing a health risk assessment to help employees identify potential health risks. Within this group, 22 percent -- or a relatively small two percent of all employers -- offer financial incentives such as lowering the worker’s share of premiums or offering merchandise, gift cards, travel, or cash to their workers. Large firms are more likely than small firms both to offer assessments and to offer financial incentives.
- Significant increase in employee share of family health covereage costs
- Significant increase in PPO plans (combined with the virutual elimination of conventional health insurance coverage)
- Significant increase in the number of workers covered by high-deductible plans
Workers on average are paying nearly $4,000 this year toward the cost of family health coverage - an increase of 14 percent, or $482, above what they paid last year.
The jump occurred even though the total premiums for family coverage, including what employers themselves contribute, rose a modest 3 percent to $13,770 on average in 2010. In contrast, the amount employers contribute for family coverage did not increase.
Preferred Provider Organizations (PPOs) continue to dominate the employer market, enrolling 58 percent of covered workers. Average PPO family premiums topped $14,000 annually in 2010.
Since 2005, workers’ contributions to premiums have gone up 47 percent, while overall premiums rose 27 percent, wages increased 18 percent, and inflation rose 12 percent.
Many employers are also raising the annual deductibles workers must pay before their health plans begin to share most health care costs. A total of 27 percent of covered workers now face annual deductibles of at least $1,000, up from 22 percent in 2009. Among small firms (3-199 workers), 46 percent face such deductibles.
30 percent of employers say they reduced the scope of health benefits or increased cost sharing, and 23 percent report increasing the amount employees pay for coverage.
Among other plan types, only consumer-driven plans (which are high-deductible plans that also include a tax-preferred savings options such as a Health Savings Account or Health Reimbursement Arrangement) saw growth in their market share. Such plans now enroll 13 percent of covered workers, up from 8 percent last year.
Other findings include:
• Single coverage. The survey also tracks the premiums for worker-only health benefits, which increased 5 percent in 2010 to reach $5,049 annually. Workers on average are paying $899 annually for single coverage, up from $779 in 2009. Forty-seven percent of covered workers are in single coverage plans.
• Physician office visits. Among covered workers with a copayment for in-network physician office visits, the average copayment increased a small but statistically significant amount from 2009 to 2010 -- from $20 to $22 for primary care and from $28 to $31 for specialty care.
• Mental health benefits. In response to the 2008 Mental Health Parity and Addiction Equity Act, 31 percent of firms with more than 50 workers made changes to the mental health benefits they offer. Most of this group eliminated limits on coverage to comply with the law, though a small share (5 percent of those making changes) dropped mental health coverage altogether.
• Wellness benefits. About three-fourths (74 percent) of employers offering health benefits offer at least one of the following wellness programs: weight loss program, gym membership discounts or on-site exercise facilities, smoking cessation program, personal health coaching, classes in nutrition or healthy living, web-based resources for healthy living, or a wellness newsletter.
• Health risk assessments. Among firms offering coverage, 11 percent give their employees the option of completing a health risk assessment to help employees identify potential health risks. Within this group, 22 percent -- or a relatively small two percent of all employers -- offer financial incentives such as lowering the worker’s share of premiums or offering merchandise, gift cards, travel, or cash to their workers. Large firms are more likely than small firms both to offer assessments and to offer financial incentives.
Thursday, September 2, 2010
Health Wonk Review - In the Here and Now
Hank Stern at Insureblog fires up Health Wonk Review - the best of the healthcare policy blogosphere.
Labels:
Health Wonk Review
Subscribe to:
Posts (Atom)